
In today’s digital landscape, phishing remains a significant threat to organizations, often leading to data breaches and financial loss. While many companies are aware of standard anti-phishing measures, fewer know about the powerful tools available within Google Workspace (GW). Specifically, GW administrators can set up advanced email filtering rules, also known as content compliance rules, to mitigate phishing risks effectively and create effective phishing attack prevention mechanism.
Understanding Content Compliance in Google Workspace
As a Google Workspace administrator, you can create rules to manage email content that matches specific criteria. This advanced feature, known as content compliance, allows you to filter messages based on predefined sets of words, phrases, text patterns, or numerical patterns. These rules can be configured for simple matches, advanced matches, and metadata matches.
An often-overlooked aspect of content compliance is its potential use as an anti-phishing tool. Here’s how you can implement content compliance rules to protect your organization from phishing attempts.
Step-by-Step Guide to Setting Up Anti-Phishing Rules
1. Navigate to Content Compliance Settings. To set up content compliance rules:
- Go to Apps > Google Workspace > Gmail > Compliance.
- Select Content compliance and click Configure.
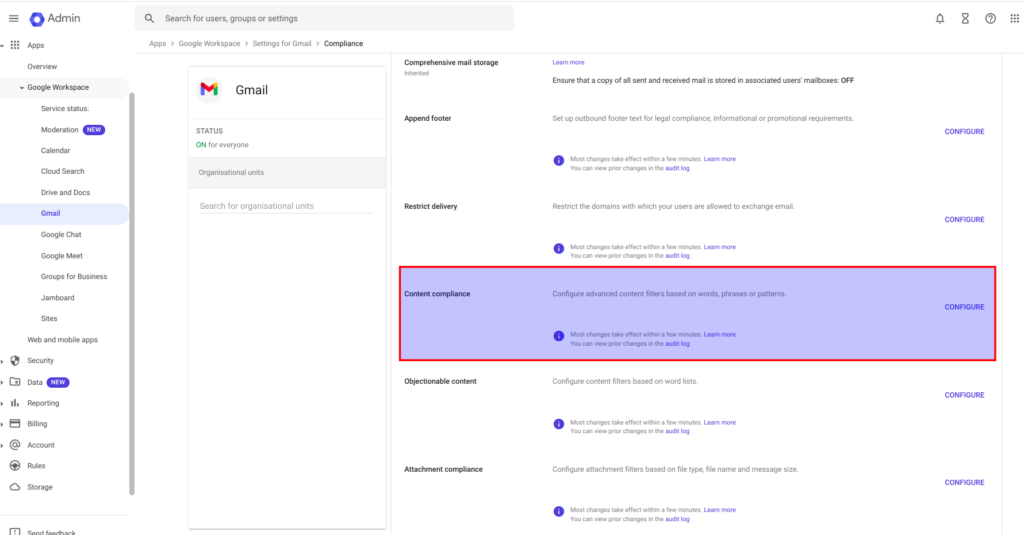
2. Define Inbound Email Rules. In the settings modal that appears, configure the rule as follows:
- Email messages to affect: Select Inbound.
3. Add Expressions for Content Matching. This section allows you to specify the criteria for emails:
- Under Add expressions that describe the content that you want to search for in each message, choose If ALL of the following match the message.
- Click Add to open a new modal for setting up content matching criteria.
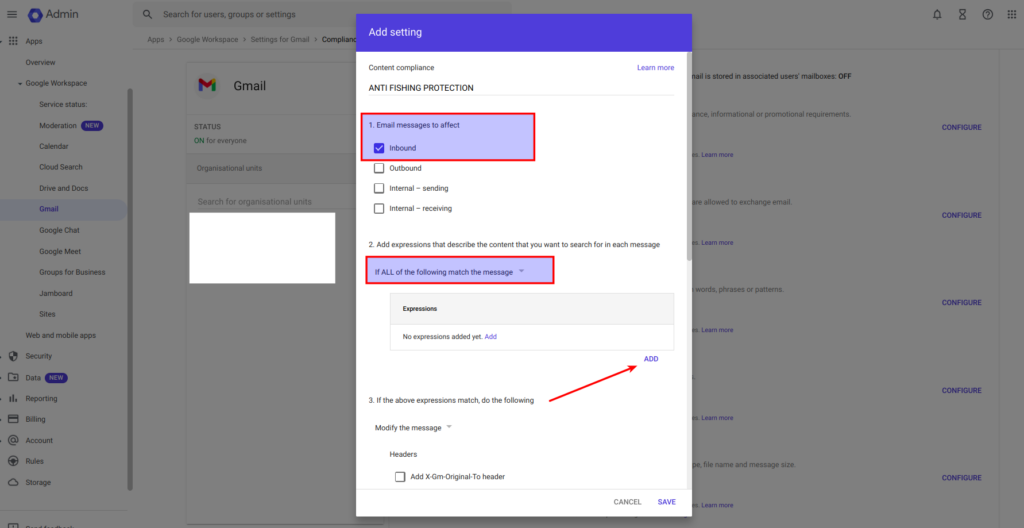
4. Create the First Rule – Matching URLs:
- Choose Advanced content match
- Location: Select Body.
- Match type: Choose Contains text.
- Content: Input a regular expression that matches any URL (adjust it to your requirements):
https?:\/\/(www\.)?[-a-zA-Z0-9@:%._\+~#=]{1,256}\.[a-zA-Z0-9()]{1,6}\b([-a-zA-Z0-9()@:%_\+.~#?&//=]*)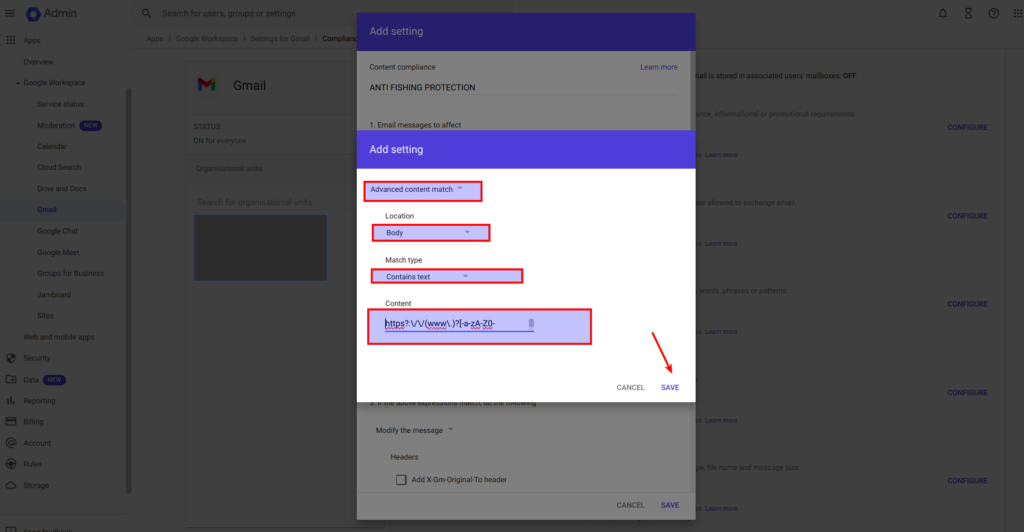
5. Create the Second Rule – Whitelist Trusted Domains. Similarly, click Add and set up another expression:
- Choose Advanced content match
- Location: Select Body.
- Match type: Choose Does not contain text.
- Content: Input a regular expression to whitelist trusted domains. Here’s an example for Google and Amazon domains:
^https:\/\/(www\.)?(google|amazon)\.This will ensure that URLs from Google and Amazon are not flagged. You can add more trusted domains following the same pattern. Sure, it is only the example, make sure to include all domains that belong to your company and any other trusted resources.
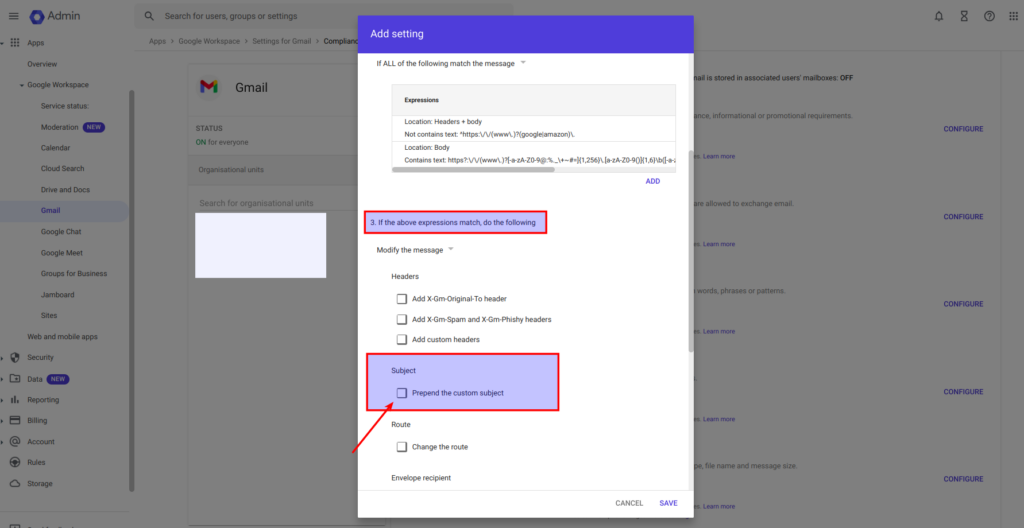
6. Configure the Action for Matching Emails. Once the expressions are set up:
- Under If the above expressions match, do the following, choose Modify the message.
- In the Prepend custom subject field, add a marker such as “External” to the email subject. This will allow to alert employees that the email contains links to domains outside of your trusted list.
Why This ANTI FISHING TRICK Works
By implementing this configuration, any inbound email containing URLs that don’t match your trusted domains list will be flagged with custom suffix to it’s subject. The “External” marker in the subject line serves several important purposes:
- Immediate Awareness: Employees will instantly recognize that an email contains links to external sites. This heightened awareness can prompt them to scrutinize the email more carefully before clicking on any links.
- Suspicious Link Detection: If an email with the “External” marker appears to be from a familiar source (like your company) but still gets flagged, it signals that the URLs might be misleadingly similar or malicious. For example, a phishing email might seem to come from your company but actually link to a malicious site that mimics your company’s branding.
- Enhanced Vigilance: The visible warning helps foster a culture of security awareness among employees. It reminds them to exercise caution and use best practices when interacting with emails containing external links.
Though be careful with current practice – in case almost every email would be flagged – then nobody will pay attention at it. Current practice is mostly suitable for companies with minimized external correspondence relatively to the internal number of emails. It is also essential to configure white lists properly – to cover all resources you consider to be trusted and which is commonly used at your organization. That is quite complicate task, that will require from Google Workspace admin a lot of adjustments, good knowledge of how all company works and what it use at everyday work. Hope that you found current article to be useful. Best regards.
P.S.
In case you are interested more at cyber security for web applications, then welcome to my course: “DevSecOps: How to secure web application with AWS WAF and CloudWatch“. Here you may find coupon with discount.
