Hi, cyber security fans. That is the introduction to the AWS WAF topic. At current article I will try to explain briefly what is AWS WAF and how it works. Here you will also find different links, that will allow to investigate current theme more deeply. Please, remember, that according links will appear gradually – one more article within 2-3 weeks. In case you would like to be become expert at AWF WAF, I recommend to signup to my newsletter – that will allow to get information in time, without need of regular checks for the current post. Let’s start our trip from the question: What is WAF at all?
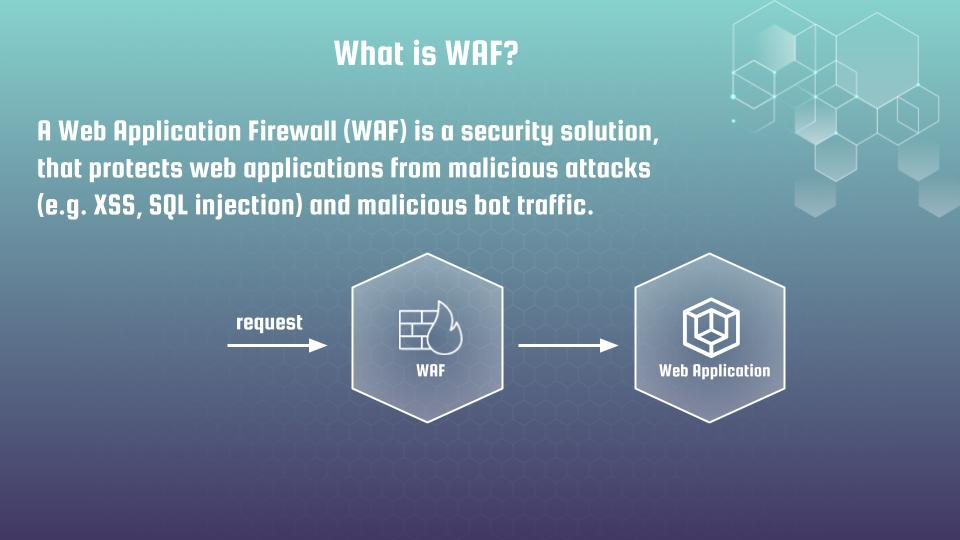
A Web Application Firewall (WAF) is a security solution that protects web applications from malicious attacks (e.g. cross-site scripting, SQL injection) and malicious bot traffic. WAF is typically deployed as a reverse proxy, sitting between the internet and the web application, to inspect and filter incoming requests before they reach the web server.
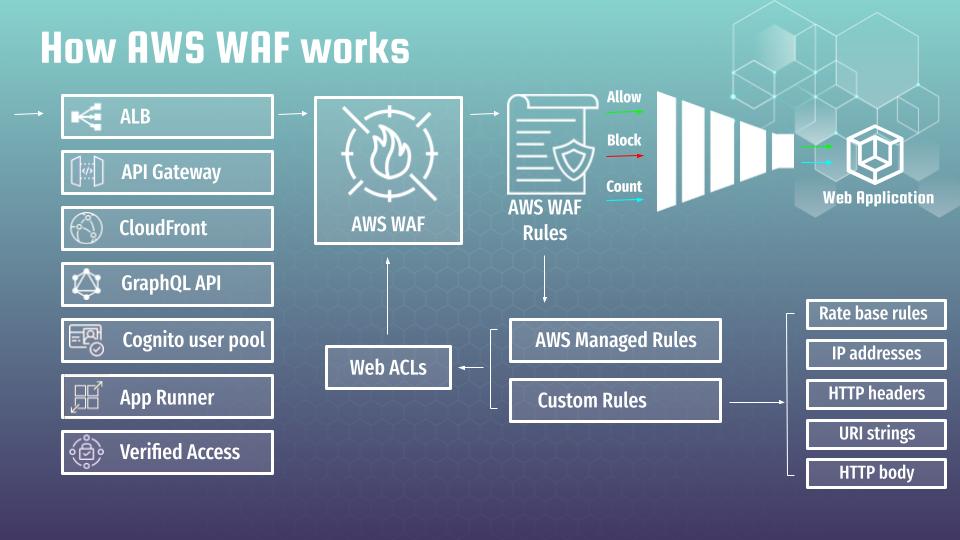
AWS WAF is a cloud-based solution, providing a comprehensive set of security rules to protect web applications. Here is how it works.
First of all we have to define the resource type to which we want to attach AWS WAF. The most typical cases are:
- Application Load Balancer (ALB)
- API Gateway
- CloudFront
- GraphQL API
- Cognito user pool
- App Runner
- Verified Access
The essential thing is that resource type does not change how AWS WAF works or how it should be configured. In my course “DevSecOps: How to secure Web App with AWS WAF and CloudWatch” I am showing in details how to attach WAF at ALB, what are the best AWS WAF practices and how AWS WAF works at real practice by imitating different hackers attacks at test Flask application. That is good point were you can start from. All you will learn at at load balancer example, can be used completely the same at any other AWS service mentioned above. By the way – you may find the Udemy coupon with best price and my blog page devoted to the course. Or you can continue the reading 🙂
The main components of AWS WAF are security policies that will determine types of traffic you want to allow or block from reaching your web application. Such policies are called AWS WAF Rules. There are 2 main types of rules:
- First of all it is AWS WAF managed rules, which are pre-built managed policies that offer protection against common web attacks such as SQL injection, cross-site scripting (XSS), and much more. These rule groups are created and maintained by AWS and updated regularly to ensure they provide up-to-date protection against the latest threats. But it does not mean that you can simply turn it on and all would be working. Managed rules configuration is rather time consuming process, which requires deep understating of AWS WAF. I will try to describe the process of AWS WAF managed rules configuration and adjustment at several next articles.
- At second, it is AWS WAF custom rules, that allow to create WAF rate based rules, or any other rules based on various conditions, such as IP addresses, HTTP headers, URI strings, and HTTP body content. That is very interesting topic, which I will definitely describe at further articles (links will appear here when according articles would be ready).
It is also possible to group different rules in Web ACLs for multiple usage at different WAF instances. AWS WAF rules, arranged by priority factor, create something like a funnel filter for web application traffic. In case all are configured properly, the WAF should bypass all traffic, treated by the application as correct, and block all malicious requests.
But life is not perfect, that is why there is one additional interesting mode for WAF rules, which is called count. It allows to track the behavior of WAF rule like it would be turned on, but without blocking. That is a very useful feature, that allows to to adjust AWS Managed rules properly, and what is even more essential – in a safe way. I will describe it in details at further articles.
Generally speaking, WAF adjustment – that is a very time consuming procedure, which should be provided every time you are adding new applications or when you are adding new functionalities that drastically influence the income traffic structure. That is why I will devote a lot of time at explaining how to perform according tuning in optimal and the most fast way. Here is the slide that visualize above provided information:
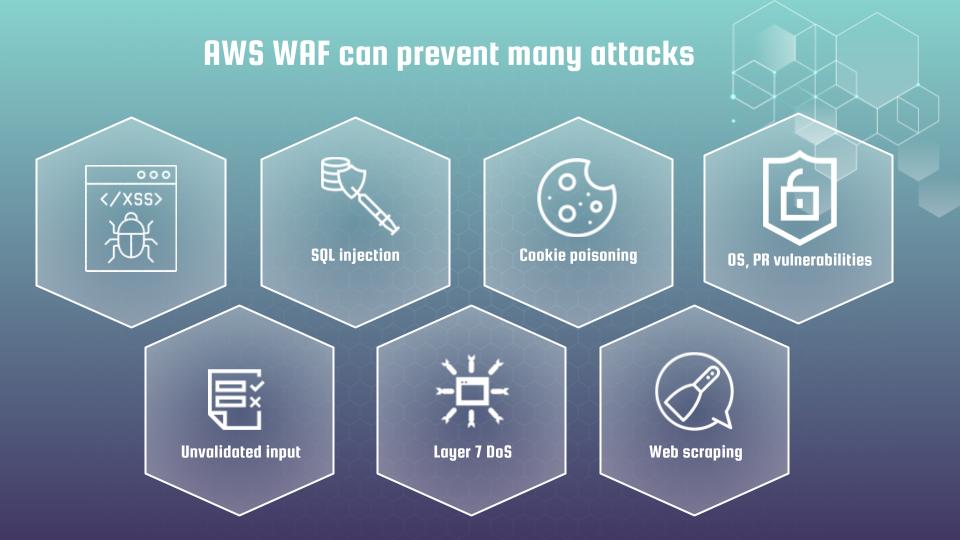
It is essentially to understand that AWS WAF is not a silver bullet that can protect you against everything. Though, yes, it is a very powerful cyber defense tool that can prevent many attacks. Such as XSS, unvalidated input, SQL injection, deny of service attacks, cookie poisoning, web scraping, OS and programming language related vulnerabilities.
Current list is definitely not full. AWS WAF is constantly evolving. More and more complicated protection mechanisms are appearing. For example, in the documentation you can find such an interesting section as intelligent threat mitigation. This is beyond the scope of the material I want to represent you, as I still did not have a possibility to test current functions at real commercial services. Though it is quite possible that situation will change that year. 🙂 Anyway I recommend you to get acquainted with those rather fresh features.
Hope, you found current article to be useful and interesting. At next article I propose to start investigation of the AWS WAF managed rules (link will appear here, when next article would be ready). If you want to pass all material faster in a more efficient way, then I propose you to view my on-line course at udemy.

