Hi, devops fan. Welcome to the 3d and last part of articles devoted to the terraform network module. Here we are going to deal with outputs, variables and finally implement terrafrom AWS network module. At 2d part we have finished at routing and security groups. Let’s continue with environment variables – terraform/modules/network/variables-env.tf:
variable "account_id" {
type = string
description = "AWS Account ID"
}
variable "env" {
type = string
description = "Environment name"
}
variable "project" {
type = string
description = "Project name"
}
variable "region" {
type = string
description = "AWS Region"
}And here are variables related to network module by itself terraform/modules/network/variables.tf:
variable "vpc_ip_block" {
type = string
}
variable "subnet_cidr_public" {
type = string
}
variable "subnet_cidr_private" {
type = string
}
variable "new_bits_public" {
type = number
}
variable "natgw_count" {
type = string
description = "all | none | one"
}
variable "new_bits_private" {
type = number
}
variable "az_num" {
type = number
description = "Number of used AZ"
}
variable "management_ips" {
type = map(string)
}
variable "app_direct_access" {
type = map(map(string))
}Finally below we have module outputs terraform/modules/network/outputs.tf:
output "vpc" {
value = aws_vpc.main
}
output "subnets_private" {
value = aws_subnet.private
}
output "subnets_public" {
value = aws_subnet.public
}
output "sg_app" {
value = aws_security_group.app
}
output "sg_management" {
value = aws_security_group.management
}
output "sg_es" {
value = aws_security_group.es
}And in the end we have implementation terraform/dev/network/main.tf. Please, remember to change x.x.x.x.at some real ip address your are going to use
terraform {
backend "s3" {
bucket = "terraform-state-aws-es-devops"
dynamodb_table = "terraform-state-aws-es-devops"
encrypt = true
key = "dev-network.tfstate"
region = "eu-central-1"
}
}
provider "aws" {
allowed_account_ids = [var.account_id]
region = var.region
}
module "network" {
source = "../../modules/network"
account_id = var.account_id
env = var.env
project = var.project
region = var.region
az_num = 3
vpc_ip_block = "172.27.72.0/22"
subnet_cidr_private = "172.27.72.0/24"
subnet_cidr_public = "172.27.73.0/24"
new_bits_private = 2
new_bits_public = 2
natgw_count = "one"
management_ips = {
"x.x.x.x/32" = "VPN",
}
app_direct_access = {
"vpn" = {
"x.x.x.x/32" = "VPN",
}
}
}
Then run terraform init and apply terraform chanmges as it is represented at screen:
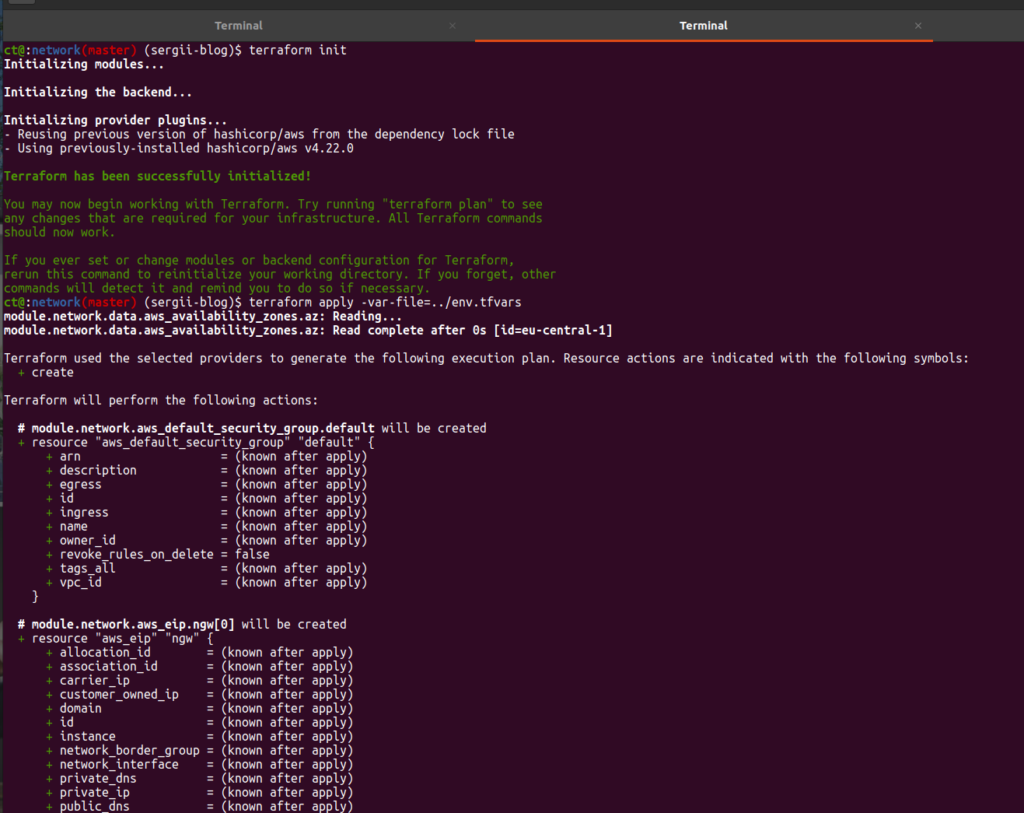
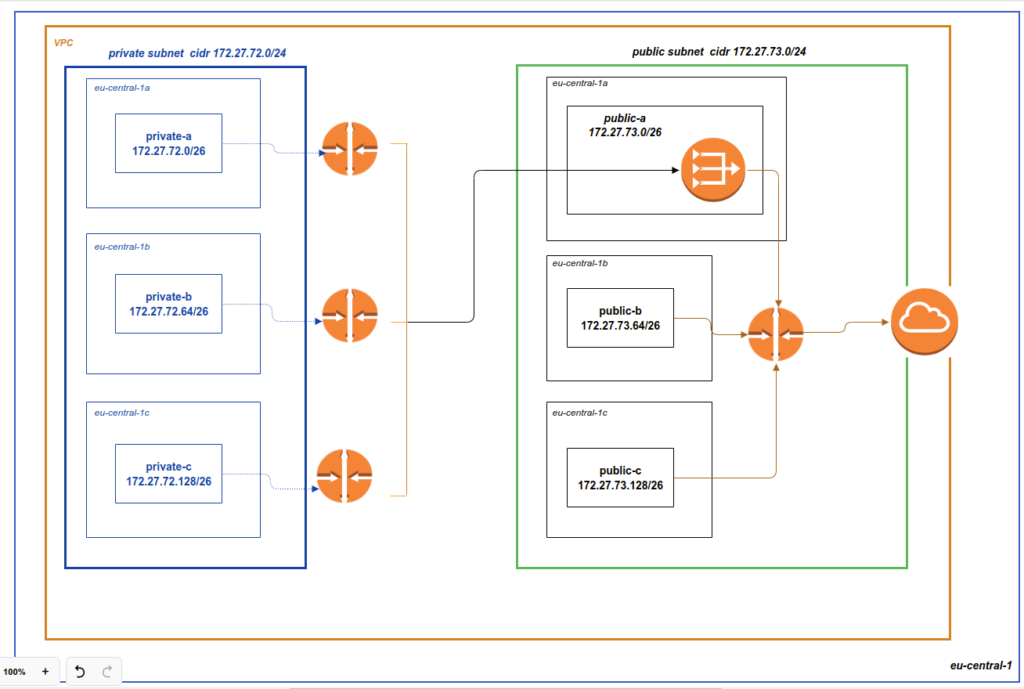
If you did all all properly – you have to see “green” success message that all resources are added. Here is, just as a reminder, our architecture scheme:
And below you can find screens from AWS console
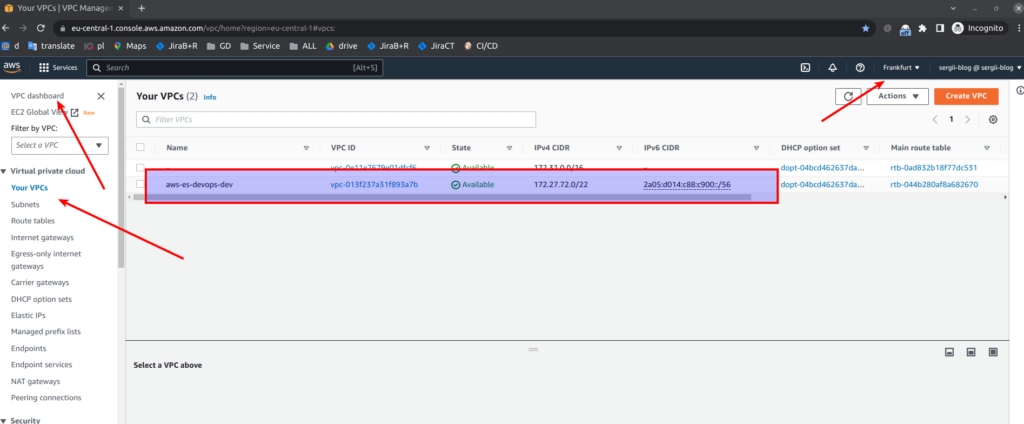
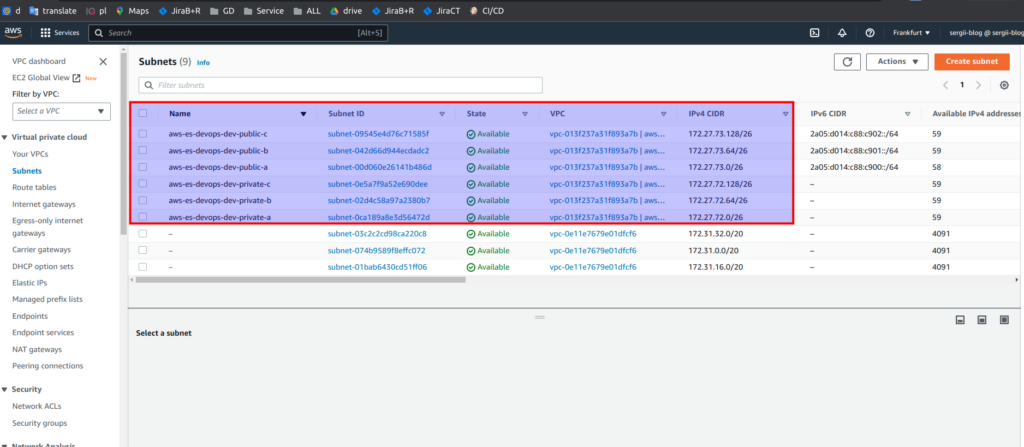
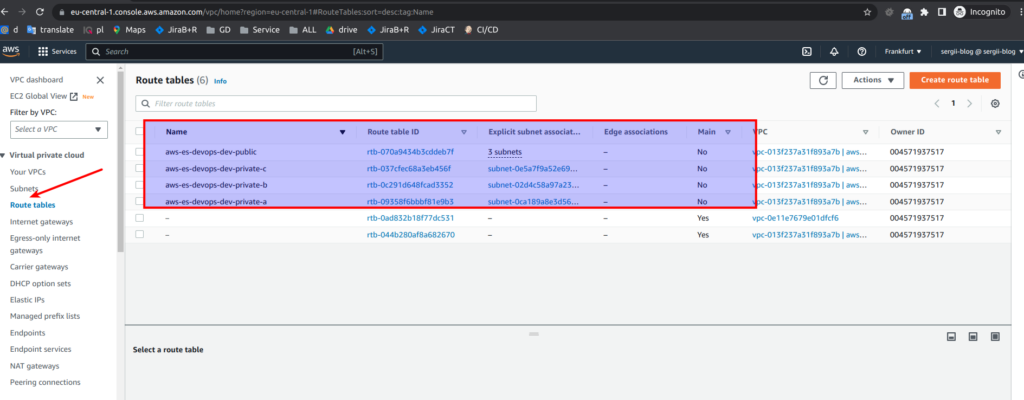
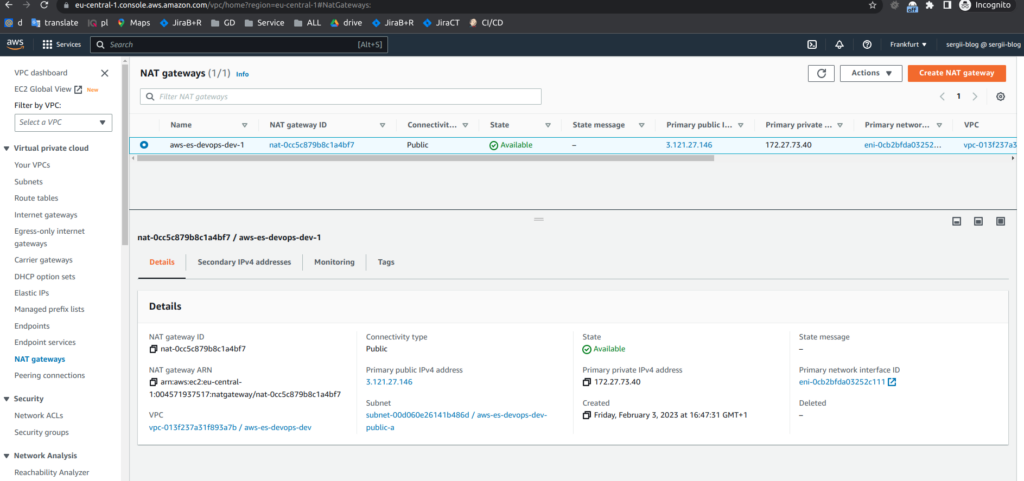
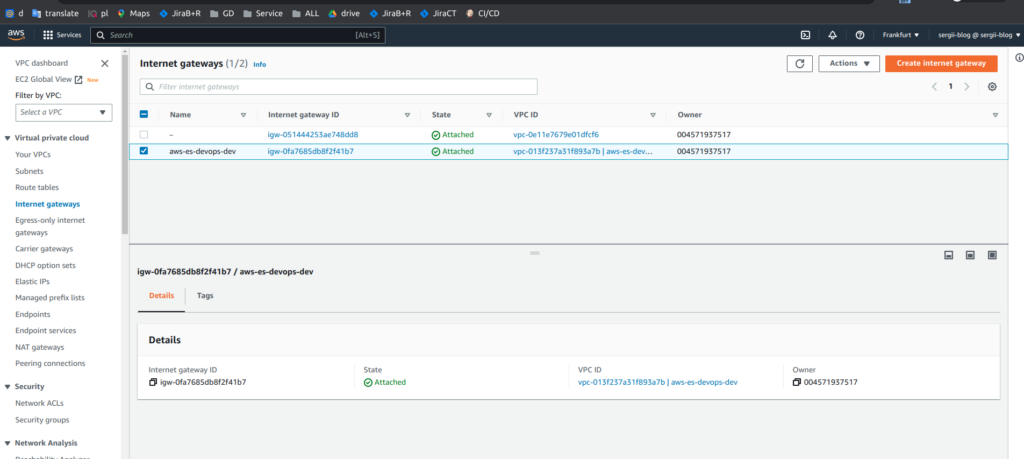
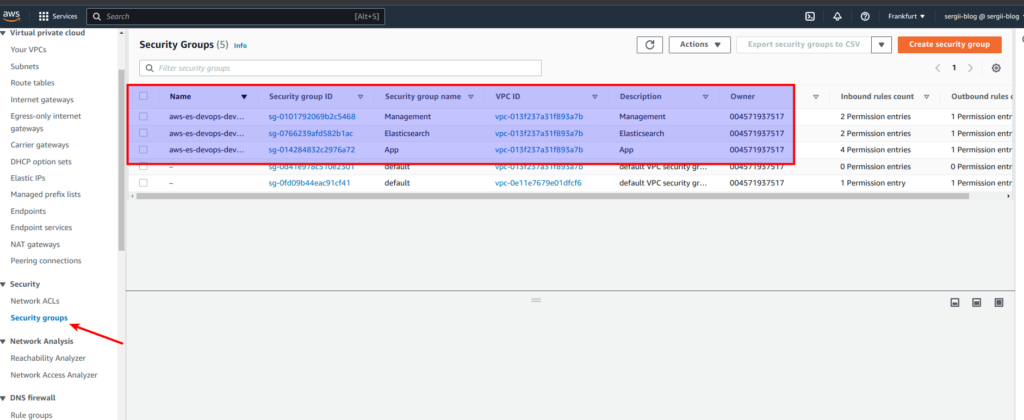
So, great. Take my congratulations. You already know how to use network terraform module that will create VPC, subnets, route tables, security groups, network address translation (NAT) and internet gateways (IG). If you still have some questions, as always, you may refer to online udemy course. As the reader of that blog you are also getting possibility to use coupon for the best possible low price. P.S. Don’t forget to destroy AWS resources in the end 😉

