Udemy Coupon with MAX discount: PHPSECURITY01 – active 01.01.2026-01.02.2026;
in case coupons are already expired, please check that page regularly – new one will appear soon
Hi, current article is a short representation of my course: “PHP REST API Cybersecurity”.
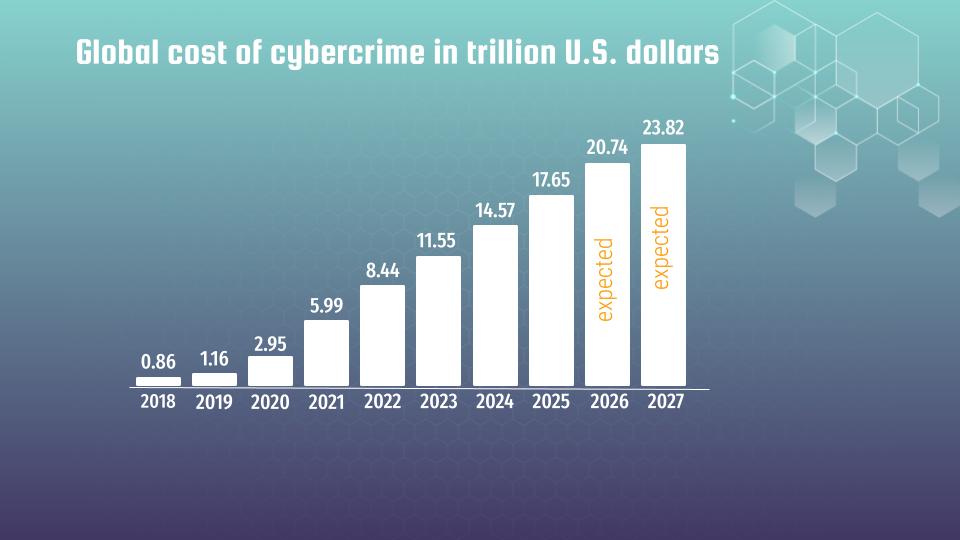
In an increasingly connected world, cybersecurity is no longer just an IT concern – it’s a critical issue that affects businesses, individuals, and entire nations. As the global landscape becomes more interconnected, and tensions between nations rise, cyberattacks are becoming more sophisticated and frequent. It’s not just about protecting against hackers; it’s about understanding how vulnerabilities in systems can be exploited, and how we can defend against them.
While many courses, articles, and conferences focus on ethical hacking and penetration testing, there’s a glaring gap in defensive security. Specifically, how do we protect the applications we build from these attacks? That’s why I’ve created this course – PHP REST API Security – to empower developers to understand both the offensive and defensive aspects of web application security, especially in the context of PHP and REST APIs.
In my 20 years of experience in cybersecurity, I’ve often wondered why there are so many courses on how to hack into systems, but so few that focus on how to protect against those attacks. The defensive side of security is significantly more complex. It’s not just about knowing how to break things—it’s about understanding the intricate details of various technologies, frameworks, and languages, like PHP, and how they work together in an application.
To be a good defender, you need to have a deep understanding of the technology you’re working with. You need to know the ins and outs of programming languages, operating systems, and infrastructure architecture. It’s a multi-faceted, more difficult approach that requires much more effort to master, which is why there are fewer experts in this area.
In this course, I’ve condensed over almost 2 decades of experience into 5 hours of practical learning, designed to help you understand the top vulnerabilities in PHP REST APIs and how to mitigate them effectively.
First several sections focuses on indirect security issues that are essential for every developer to understand. API documentation, error handling, and debugging are all areas that are often overlooked but can have a huge impact on the overall security of your system.
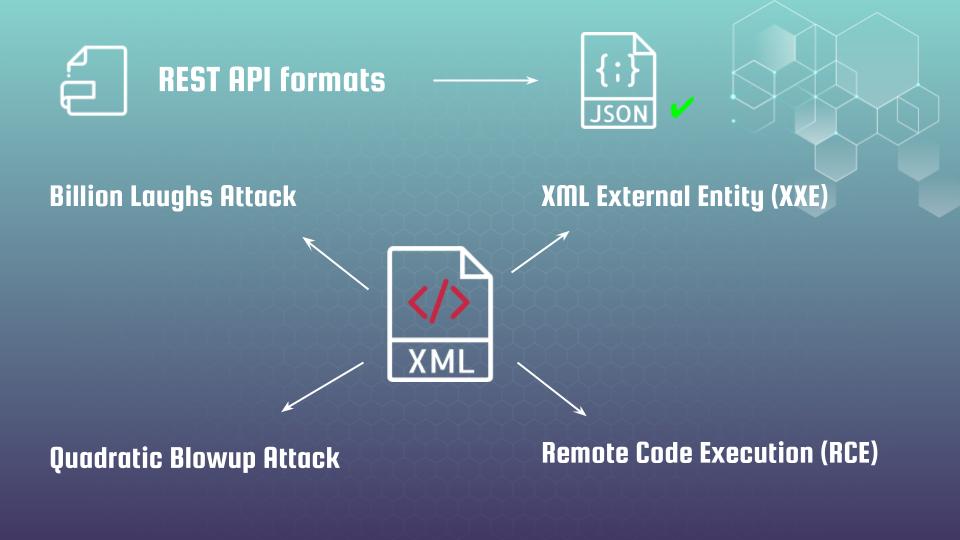
At next step the most popular formats for APIs would be discussed, with a quick dive into why JSON is generally the safest and why XML is far from a good choice. You will learn in details on practice about Denial of service XML attacks such as Quadratic Blowup Attack and Billion Laughs Attack, smoothly going with XML External Entity attacks and finishing with Remote Code Execution (RCE).
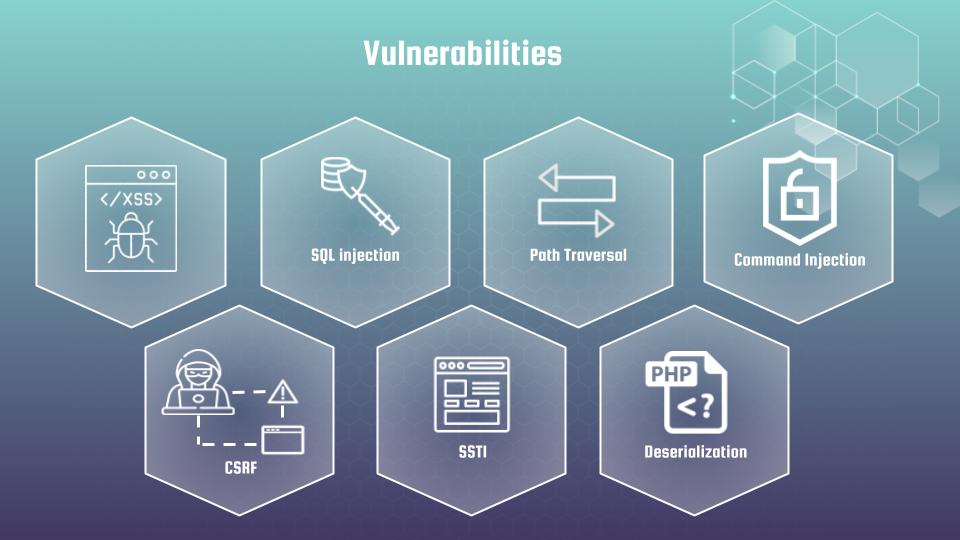
Then I am passing over the most popular vulnerabilities and explore how to mitigate them with hands-on examples. The course covers such topics as:
- XSS attacks – reflected, stores and file-based types
- CSRF
- SQL injection – union, blind content and time based vectors
- Template injections
- Path Traversal
- Incredibly tricky theme of PHP deserialization and how it can be used as vulnerability
- Command Injection – here I’ll reveal a zero-day case from my recent work. And explain why red teams often have the upper hand over blue teams, and why it’s impossible to be 100% safe – even with perfect security practices.
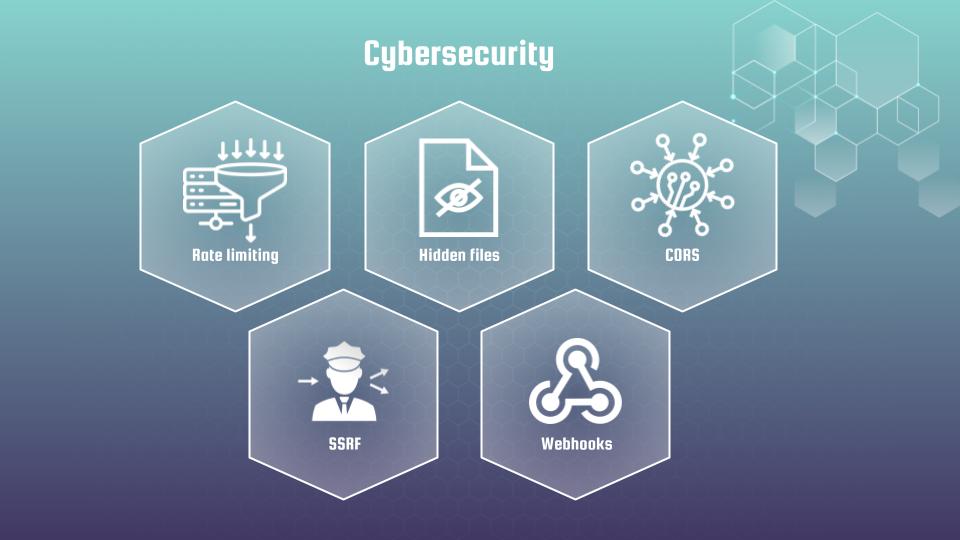
Every concept is paired with practical coding exercises. For each vulnerability, we’ll recreate attacks, so you can feel them firsthand, then apply the best practices to defend against them. That is far from all, as course also icludes such essential cybersecurity issues as:
- Rate limiting
- Server-side request forgery (SSRF)
- Hidden files
- Webhooks
- Cross-Origin Resource Sharing (CORS)
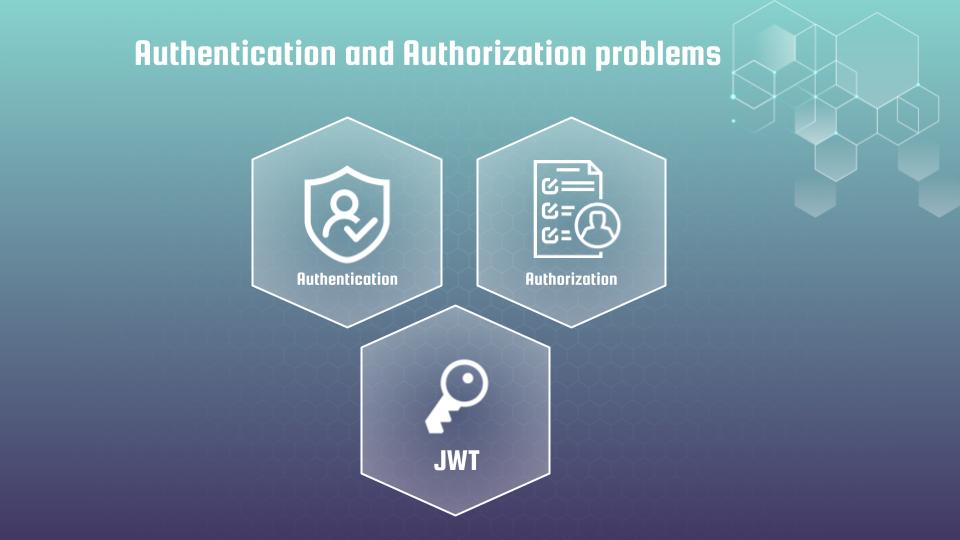
There are also detailed sections about authentication and authorization problems, special focus is devoted to the JSON Web Token (JWT) vulnerabilities.
By the end of this course, you’ll have a solid understanding of how to secure PHP REST APIs from top to bottom. Whether you’re a beginner or an experienced developer who wants to fill in the gaps, this course is designed to give you a complete picture.
If you’re ready to step up your security skills and become part of the blue team, hit that enroll button, and let’s dive into the world of PHP REST API security together.
