Hi, cyber security fans.
At current, and several more parts, we will speak in details about AWS managed rules. That is very powerful web application security solution, but it is not so easy to configure and apply it properly, especially for enterprise products with high traffic volume. AWS managed rules – that is a list of firewall application policies, which are aimed to protect web application against different security risks. The AWS team provided a really good job to create such a ready firewall rule set solution. Let’s view together core rule set as an example to understand better how it works. The core rule set (CRS) contains rules that aimed to protect web application against OWASP Top Ten security risks. Please, view the table with different rules at documentation for a while and return back.
Hope, you already have initial feeling how powerful AWS core rule set is. Let me show you several screens from my on-line course “DevSecOps: How to secure Web App with AWS WAF and CloudWatch” to demonstrate how all looks from AWS console side.
So, within a course I’ve added 10 different WAF rules, 4 of them were from AWS managed list:
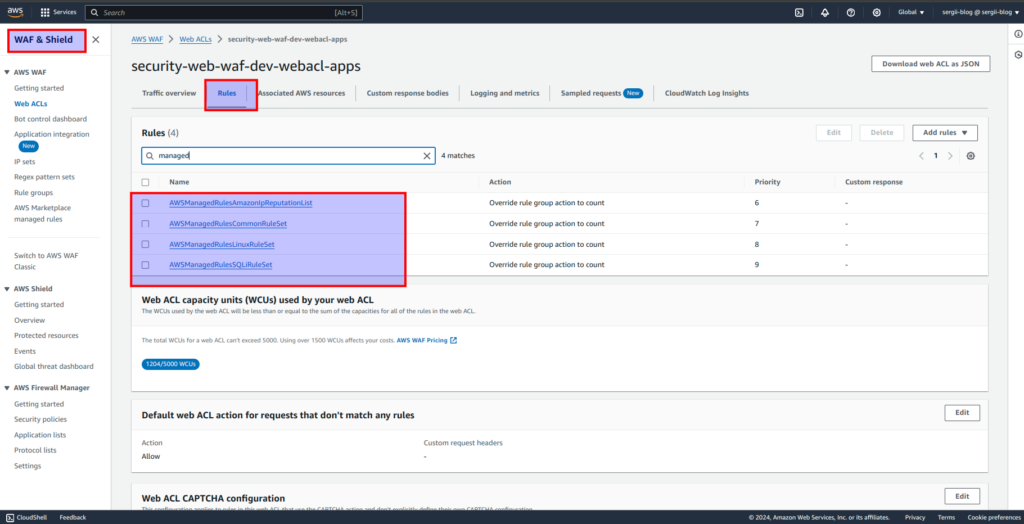
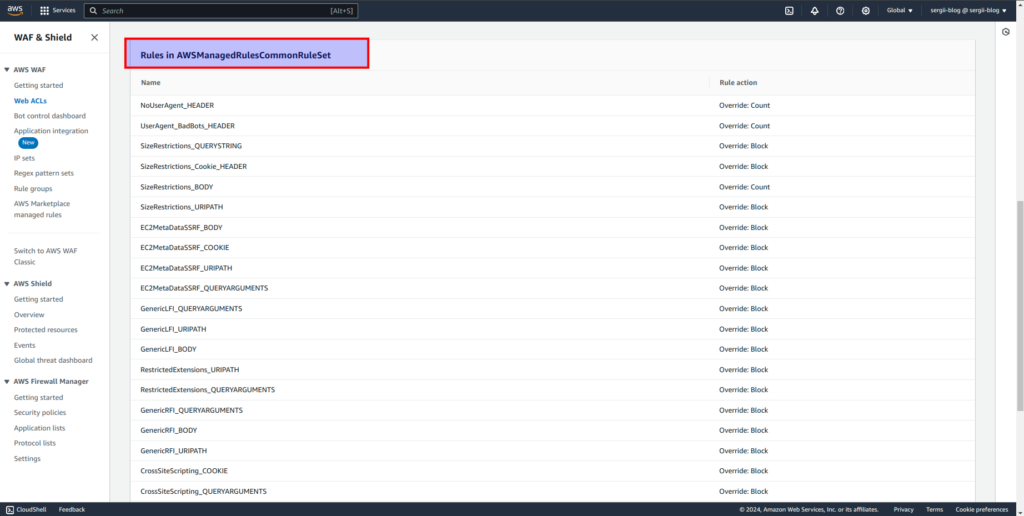
While going inside to AWS managed WAF rules set, we will see the next picture:
If you will check AWS WAF console, you will notice, there are much more then 4 WAF managed rule sets. Here is the screen with only some part of all available options:
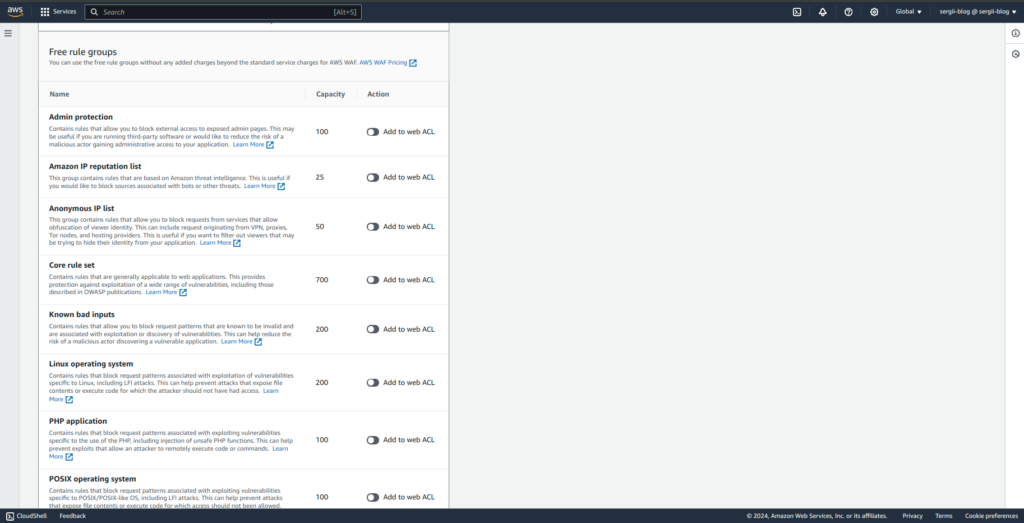
So, reasonable question appears – can we add all of them? The answer is – NO 🙁 There are 2 reasons for that.
- At first, not all rule groups are suited for concrete application tech stack. For example at course, I am using Python+Flask application to demonstrate different malicious requests and how AWS WAF deals with that. In that case, adding e.g “PHP application” WAF rule set does not appear to be a reasonable decision. Another example – there is not sense to add “Windows operation system” rules in case you are using Linus OS as running environment for web application. So, it is always a good idea to view every rule and decide what is really useful for your exact case.
- There is also one more, less obvious thing – please pay attention to the 2d column from screen above, it is called capacity. You may read in details about it at AWS documentation. In practice it means that in such a way AWS limits resources we can use. If you need more capacity then it is included in the base package – then you will have to apply at AWS support with ask to increase that limit, moreover – you will have to pay for it additionally. So, it is better to add only managed rules you really need and leave some capacity for custom rules, which we will talk about a little bit later.
Ok, let’s assume that you chose all managed rule groups that are suited for application, e.g as I’ve chosen 4 concrete rules for test Flask app. You may say now “Wow cool, finally we can turn it all on and be satisfied with the work to be done”.
Unfortunately you can’t simply apply all those rules and be happy. Suppose you are a little bit confused now. Let me explain to you why you can’t do it. The main problem here is false positives. If you will apply several AWS managed rule groups for real application, then you will definitely block not only malicious, but also useful traffic. Within the last year I applied different WAF managed rules at 5 different applications – one of them is really huge, one middle, and 3 can be considered small. All of them are completely different, but in all cases I had false positives.
And it is completely OK. AWS managed rules are really good, but together with that they are too broad. But we can and have to use it, simply it will require some additional work from our side. That work is really time consuming and for sure not the most interesting in the world. But the results that you will reach in the end can be really spectacular.
Let me share with you methodology that appeared from my commercial practice. Current approach will help you to apply and which is even more essential – to control AWS managed rules in a safe way. I suppose it would be really useful and will help you save a lot of time. Hope you are excited to make a deep dive at WAF managed rules configuration using Terraform. Let’s do it at the next article
If you are not ready to wait, or prefer to pass all material in a fast and more convenient way – then welcome to my course, were you can pass all material in a fast and convenient way. Here you can find coupon with discount, which I am updating regularly in the middle of every month.
